Описание
Dragonfly2 has hard coded cyptographic key
Summary
Hello dragonfly maintainer team, I would like to report a security issue concerning your JWT feature.
Details
Dragonfly uses JWT to verify user. However, the secret key for JWT, "Secret Key", is hard coded, which leads to authentication bypass
PoC
Use code below to generate a jwt token
And send request with JWT above , you can still get data without restriction.
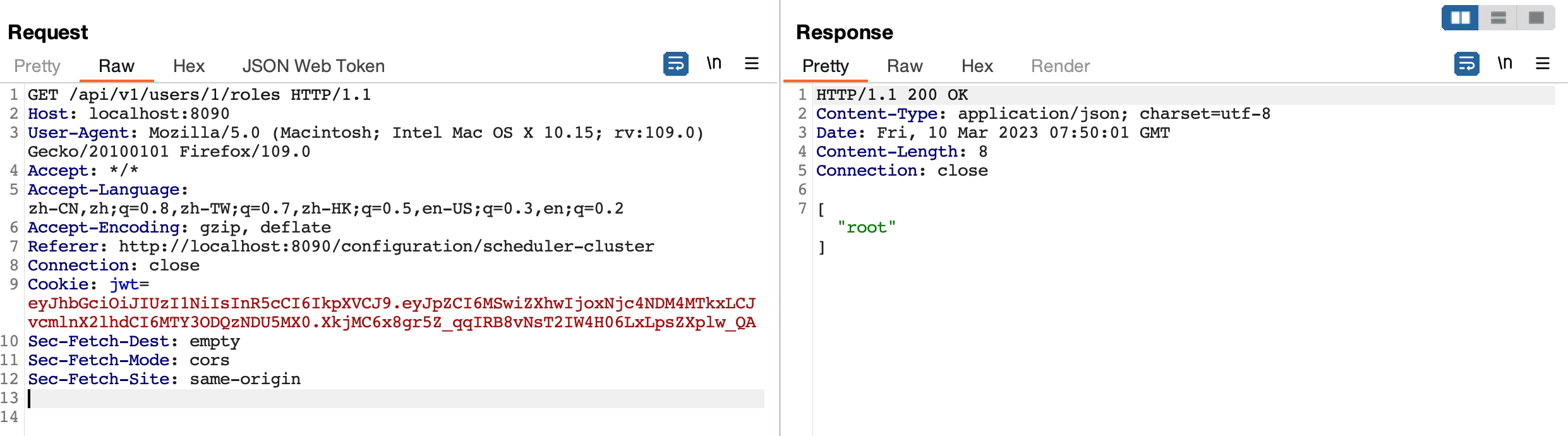
Impact
An attacker can perform any action as a user with admin privileges.
Ссылки
- https://github.com/dragonflyoss/dragonfly/security/advisories/GHSA-hpc8-7wpm-889w
- https://nvd.nist.gov/vuln/detail/CVE-2023-27584
- https://github.com/dragonflyoss/Dragonfly2/commit/e9da69dc4048bf2a18a671be94616d85e3429433
- https://github.com/dragonflyoss/dragonfly/commit/684469a31bd27d38c715c507bca9f6d2c21f9007
- https://github.com/dragonflyoss/Dragonfly2/releases/tag/v2.0.9
Пакеты
d7y.io/dragonfly/v2
>= 2.1.0-alpha.0, < 2.1.0-beta.1
2.1.0-beta.1
d7y.io/dragonfly/v2
< 2.0.9-rc.2
2.0.9-rc.2
EPSS
9.3 Critical
CVSS4
9.8 Critical
CVSS3
CVE ID
Дефекты
Связанные уязвимости
Dragonfly is an open source P2P-based file distribution and image acceleration system. It is hosted by the Cloud Native Computing Foundation (CNCF) as an Incubating Level Project. Dragonfly uses JWT to verify user. However, the secret key for JWT, "Secret Key", is hard coded, which leads to authentication bypass. An attacker can perform any action as a user with admin privileges. This issue has been addressed in release version 2.0.9. All users are advised to upgrade. There are no known workarounds for this vulnerability.
EPSS
9.3 Critical
CVSS4
9.8 Critical
CVSS3